In an era where technology propels the healthcare industry forward, the recent Cybersecurity and Infrastructure Security Agency (CISA) advisory, unveiled on December 15, 2023, serves as a guiding light through the complex waters of cybersecurity. As we witness an increasing reliance on digital solutions in the healthcare and public health (HPH) sector, the need for fortified cyber resilience has never been more critical.
Understanding the Waters: Key Findings from CISA's Risk and Vulnerability Assessment (RVA)
CISA's Risk and Vulnerability Assessment, conducted in early 2023, unearthed potential vulnerabilities that ripple through the HPH sector. Beyond mere identification, these vulnerabilities, once exploited, can cast a shadow on the confidentiality, integrity, and availability of vital healthcare services. The impact extends beyond the immediate shores of HPH organizations, posing challenges for critical infrastructure and the software manufacturers steering the digital ship.
Charting the Course to Resilience: Mitigation Recommendations for HPH Organizations
A tailored approach to cybersecurity is essential in the diverse ecosystem of HPH organizations, each facing unique challenges. CISA's advisory provides not only a strategic map but detailed navigational instructions. Three core mitigation strategies—asset management and security, identity management and device security, and vulnerability, patch, and configuration management—serve as the compass. With a nuanced understanding, organizations of all sizes can now embark on the journey to enhance their cyber defenses.
CISA's Deputy Director, Nitin Natarajan, lends his perspective on the impact of common vulnerabilities on healthcare organizations. His words echo urgency, emphasizing the need for swift implementation of recommended actions to reduce cyber risk. Furthermore, his call for alignment with the Principles and Approaches for Secure by Design Software underscores the importance of building resilience into the very foundations of healthcare technology.
"Exposure of common vulnerabilities and insecure configurations can result in detrimental cyber activity for U.S. healthcare organizations, such as ransomware, data breaches, or denial-of-service. The intent of this advisory is to help organizations maintain the availability, confidentiality, and integrity of their critical healthcare and public health systems, functions, and data," emphasized Natarajan in a recent article titled "CISA Releases Key Risk and Vulnerability Findings for Healthcare and Public Health Sector."
An effective cybersecurity strategy is not a lone voyage but a collaborative effort. The advisory seamlessly integrates with existing CISA resources, such as the Healthcare Cybersecurity Toolkit and the Mitigation Guide for HPH Sector. This integration ensures that organizations can leverage a holistic approach, mapping mitigations to Cross-Sector Cybersecurity Performance Goals (CPGs).
> Access the CPG Checklist here.
Forging Ahead: Guidance for Software Manufacturers
The responsibility of steering the ship isn't solely on the shoulders of HPH organizations. Software manufacturers play a pivotal role in securing the digital future of healthcare. The advisory extends a hand to these manufacturers, providing guidance on aligning with secure design principles. Urgent steps are outlined for the secure design, development, and delivery of products—a collective effort co-sealed by 18 U.S. and international agencies. As we navigate these cyber waters, a unified call to action echoes. HPH entities are encouraged to not only review the advisory but to implement the recommended mitigations promptly.
Anchoring Resilience
In conclusion, successfully navigating the intricate landscape of technological collaboration underscores the importance of partnering with VectorUSA. Opting for VectorUSA as your technology solutions integrator is a key decision that seamlessly aligns with the NIST Cybersecurity Framework. This framework serves as a crucial tool in addressing vulnerabilities identified in CISA's Risk and Vulnerability Assessment. Its significance lies in effectively managing assets, updating systems, monitoring security, and responding to incidents, thereby establishing a robust foundation. By engaging with VectorUSA, you not only initiate the potential for a valuable partnership but also enhance your technological capabilities, ensuring a resilient and efficient trajectory for your organization's IT infrastructure.
Start this transformative journey by scheduling a free consultation with us today. Together, we’ll explore new possibilities and chart a course toward limitless horizons.
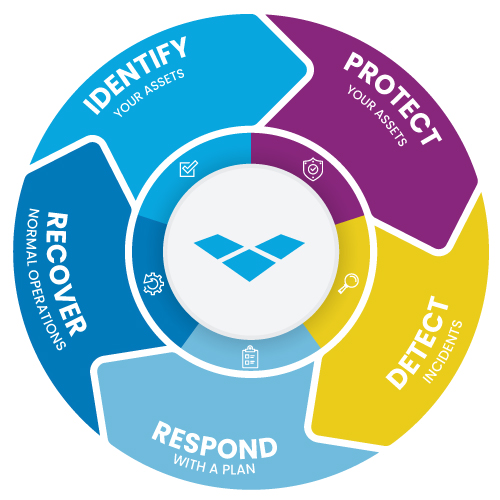
- Identify: Develop an organizational understanding to manage cybersecurity risk across systems, people, assets, data, and capabilities.
- Protect: Implement safeguards for the delivery of critical services, limiting potential cybersecurity event impact. This includes patching and proactive updating.
- Detect: Implement activities for timely identification of cybersecurity events, including Anomalies and Events, Security Continuous Monitoring, and Detection Processes.
- Respond: Take action upon detecting a cybersecurity incident, containing its impact.
- Recover: Implement activities to restore capabilities or services after a cybersecurity incident, minimizing impact. Explore comprehensive recovery solutions, including minimizing data loss (RPO - Recovery Point Objective), reducing downtime (RTO - Recovery Time Objective), implementing robust backups, and ensuring high availability (HA).
Post Topic(s): CYBERSECURITY | HEALTHCARE
